The Future of Email Protection: AI & Human
AI & Machine Learning in Email Defence

Between 75% and 90% of targeted cyber-attacks start with an email.
For hackers, email-borne attacks are the easiest and most cost-effective way to attack at scale.
However, businesses have to deal with interrupted business operations, financial and reputational damage, plus compromised business integrity.
With the number of threats continuing to rise exponentially, the World Economic Forum rates cyber attacks as one of the top five business risks facing the world.
Worldwide Information Security Spending to Exceed $124 Billion in 2019.
An increased focus on building detection and response capabilities, privacy regulations such as GDPR, and the need to address digital business risks are the main drivers for global security spending through 2019
3 of the biggest security threats
Business Email Compromise (BEC)
Here’s when an attacker impersonates an important or influential account holder, such as the Chief Executive or the Finance Director.
The attacker uses the identity of the account holder to request employees, customers or partners to make fraudulent money transfers.
BEC is sometimes described as a “man-in-the-email attack”.
BEC losses: $12 billion+ between October 2013 and May 201







Account Takeover
This is when cyber criminals target a secure account and then carry out various hacking techniques to gain access to the account.
Once inside, they may use the account to access internal company files, sensitive data or valuable financial information. Or they may use it to gather additional information they can use to launch a subsequent and more damaging attack.
HR is a popular target; hackers may sell employees’ personal data, for example. Finance is another top target; cyber criminals will use a senior executive’s account to send emails requesting payments ‘urgently’.
Spear Phishing
Spear phishing emails often don’t contain malicious links or attachments.
That’s why traditional email security solutions can struggle to identify an attack.
What’s more, the emails are more likely to land in an inbox – rather than spam or junk. Hackers often use free personal email services with relatively higher sender reputations.
3 Ways Email Attacks Prey on Human Psychology
There’s something that these attack methods have in common. It’s the reason they’re so effective (and problematic for IT leaders). Namely, they all rely on the human element, playing on the following psychological triggers:
1) Seniority
The email appears to come from the CEO, from a domain similar to the real domain. The recipient is more likely to feel under pressure, and less likely to question its veracity.
2) Urgency
There’s usually some form of urgency associated with these. The idea is to force the employee to make a judgment quickly, and less likely to pause to check with their security team.
3) Context
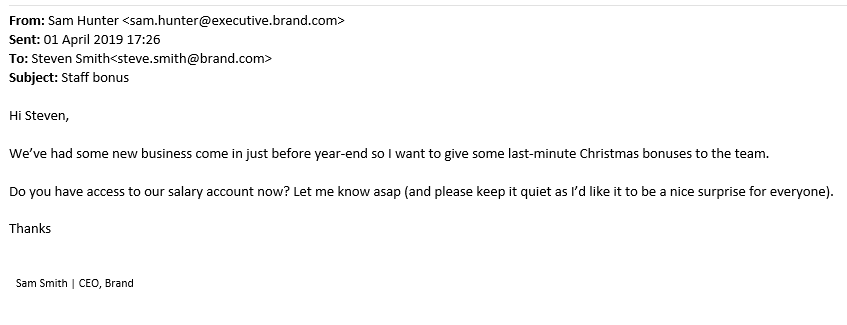
Here’s how these attacks take on a new dimension, compared to a brute force attack, for example. The email may explain why the recipient needs to take action now, citing end-of-year bonuses or gift card for clients at Christmas.
Example
In an ideal world, a malicious email would be stopped from ever landing in your inbox. However, there will be times when this happens. The following should happen when an email lands in your inbox – at the very minimum:
- Virus scanning
- Spam scoring
- Real-time intent analysis
- URL link protection
- Reputation checks
- Full cloud backup and recovery of every email and file
A question of compliance
The introduction of the EU’s General Data Protection Regulation (GDPR) has asked new questions of those responsible for corporate governance. Rather than being a finance issue, GDPR compliance is something that involves IT, HR, and the wider organisation.
That’s why email protection also needs to come with proper forms of archiving that happens across your organisation. This way you demonstrate your business is operating in a compliant manner, while also ensuring you minimise any ongoing legal risk. Features should therefore include:
Secure cloud-based archiving for meeting evolving and stringent compliance requirements and address e-discovery requests.
Email retention policies to ensure that important emails are safely archived to Barracuda’s secure cloud. Custom reports make it easy to demonstrate compliance with retention regulations and to defend deletion policies.
Next-generation protection
Traditional email gateways use static rules and policies—reputation analysis, blacklists, and malicious payloads—to determine if an email is malicious.
However, socially engineered emails such as spear-phishing attacks are designed to evade these policy-based security measures.
Adding a human layer to your email protection

2.93 million cyber security positions unfilled
“The shortage of cybersecurity professionals around the globe has never been more acute
(ICS)2

You need a human element to work with your AI. However, it’s not as simple as just hiring more cyber security professionals. Over 60,000 new malware variants are being introduced daily, so traditional signature database-based techniques can’t keep up.
Help your employees by applying some artificial intelligence that will protect them at scale. The most effective way to stop these types of attacks is using an AI-based email security solution, which understands the specific context of the organization and can use it to detect anomalies.
For example, look again at that example email:
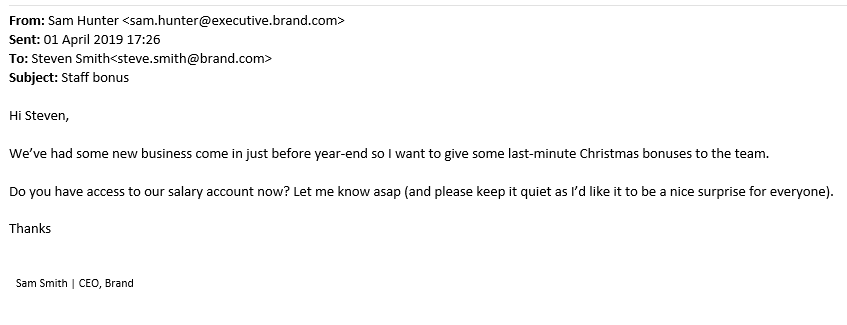
The AI can recognise that the attackers are not using email addresses normally used by the CEO, which would raise a red flag.
The AI can also pick up on the ‘asap’ and ‘last-minute’ urgent calls to action, combined with a financial transaction request.
The AI can also learn how organisations and employees communicate, to detect anomalies relating to the language or layout used.
Having said that….
…humans can still be an organisation’s weakest link when it comes to security.
For example, no amount of cyber security can guard against someone picking up the phone and handing over their password to someone they mistakenly believe to be their colleague.
Regular security awareness training and phishing simulations for employees can also help teach them how to spot this type of attack. And, if you don’t already have procedures in place spelling out how to confirm any financial requests that come in via email, whether they’re for wire transfers or gift card purchases, now is a good time to create those guidelines. It could help employees avoid making a costly mistake.
Case study example: Securing Office365
The popularity of Office365 means criminals are constantly looking for ways to bypass its systems. So consider a system that supports training your end users. For example, Barracuda Essentials Email Security Service comes with a tool called Link Protection. This automatically detects if a URL is ‘typosquatted’ (created to look similar to an existing and popular URL), or links to a website that’s known to be compromised, and warns the user.



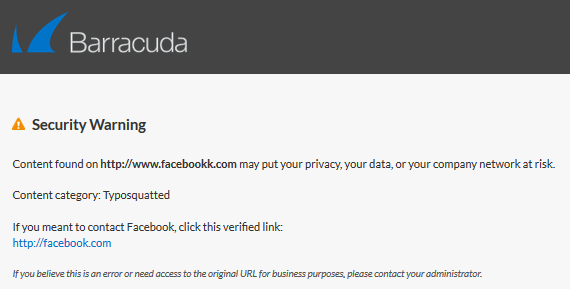
After this alert, the user can undergo a 5-minute training exercise to understand more about how the attacks work.
Human + AI working together.
This is what the future of email protection looks like.
Hackers may be able to deploy AI, but organisations can respond with AI and human insight.
Ok, there's just one more thing to add...
(drumroll please)

Stay in touch
Hey, at least we left the ‘call to action’ stuff until the very end.
This is the second in a series of chapters focusing on all things email protection related.
There’s another four to come, one released every month.
To know when the next one is published, click (or tap, we're not fussy) the button below.
Go on, let’s make this the start of an intelligent relationship.
(you'll join other digital leaders who get the latest insight on all things email protection related)